Mobile sensors are everywhere, quietly recording how users move, tilt, or hold their phones. The same data that powers step counters and activity trackers can also expose personal details such as gender, age, or even identity. A new study introduces a method designed to stop that information from being inferred in the first place, without interrupting the phone’s normal functions.
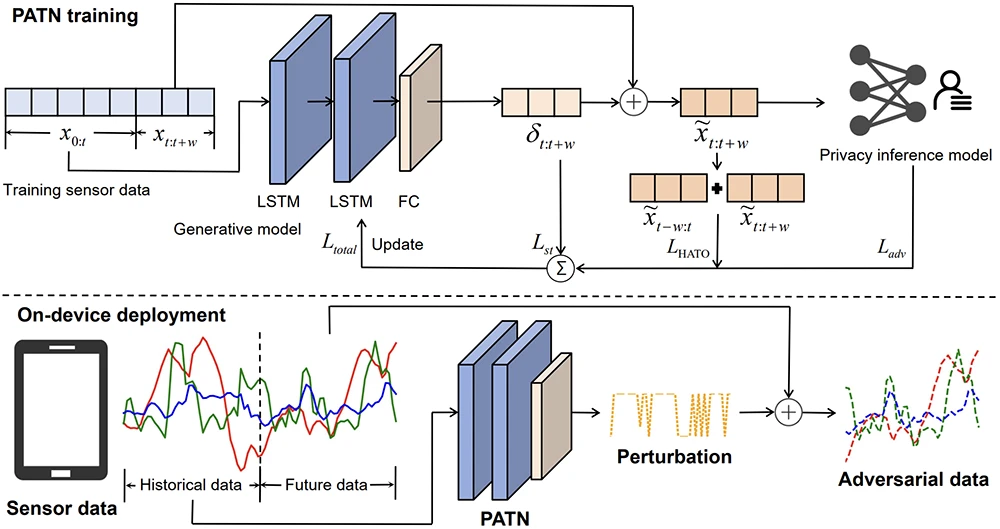
Overview of the PATN framework. The system includes PATN training, where the network learns to generate privacypreserving perturbations, and on-device deployment, where the trained model runs securely in real time.
Researchers from China and Japan have developed what they call a Predictive Adversarial Transformation Network (PATN), a framework that adds privacy protection to motion sensor data in real time.
The work targets a longstanding problem: motion sensors on smartphones are easily accessible through public APIs, which means many apps can read them without explicit permission. While this access helps features like fitness tracking, it also gives attackers or untrusted apps the chance to infer private traits by analyzing motion patterns.
The challenge of real-time privacy
Most privacy-preserving systems rely on collecting a full sequence of sensor data before applying transformations or adding noise. That delay makes them unsuitable for real-time use, since phones constantly stream data. Older techniques, such as those based on differential privacy or generative adversarial networks, tend to distort temporal and semantic information, degrading the usefulness of sensor data for ordinary applications.
PATN was designed to work differently. Instead of waiting to receive a complete batch of readings, it uses recent historical signals to predict what the next few moments of motion data will look like. It then generates adversarial perturbations (tiny, calculated modifications that mislead inference models) before the data is made available to apps. This allows privacy protection to happen instantly, with no noticeable delay for the user or the system.
How the network works
The framework uses a sequence-to-sequence neural network built on long short-term memory (LSTM) layers. The model reads historical accelerometer and gyroscope signals, summarizes them into a compressed representation, and predicts small perturbations that are immediately applied to upcoming sensor readings. These perturbations are carefully constrained so they remain imperceptible and do not disrupt normal phone functions.
To keep the perturbations realistic, PATN limits their magnitude to the natural variation found in static sensor data. In tests, the perturbations stayed within 5 percent of the mean or standard deviation of each data dimension. That keeps them within the range of natural movement noise, helping to preserve accuracy for legitimate tasks like step counting and activity detection.
The researchers also introduced what they call a history-aware top-k optimization strategy. In practice, this means the network learns to generate perturbations that remain effective even if attackers try to launch inference attempts at random points in time. By optimizing against the top few hardest attack scenarios, PATN maintains stronger protection across shifting time windows.
The team evaluated PATN using two real-world datasets: MotionSense, which tracks accelerometer and gyroscope data from smartphone users during daily activities, and ChildShield, which records motion data from users playing mobile games. These datasets are often used to train models that infer sensitive traits such as gender or age.
Consistent results across models
Because attackers may use different types of machine learning models, the researchers tested PATN’s effectiveness against several architectures, including convolutional networks, ResNet, and DenseNet. Across all of them, the framework maintained similar privacy protection levels, with attack success rates near 38 percent and EERs around 40 percent.
Further tests showed that PATN’s protection remained effective even when used against unseen or “black-box” models such as MobileNet and Xception. The system maintained comparable privacy scores across these unfamiliar architectures, suggesting strong transferability and generalization.
Balancing privacy and function
One of the key goals of PATN is to protect user privacy without breaking common mobile experiences. The experiments show that the added perturbations had negligible effects on benign functions. In step-counting tests, the difference between original and protected data was only 21 steps over thousands of readings. For human activity recognition, the change in error rate was less than two percent.
The study positions PATN as a real-time, proactive layer that fits into mobile device security frameworks. Its predictive design allows privacy protection to happen “on the fly,” aligning with how sensors operate continuously. While further testing will be needed in commercial systems, the concept shows that privacy safeguards do not have to come at the cost of usability or performance.